PCI DSS is a term that should be familiar to anyone dealing with credit card payment processing. For readers who are less familiar with the topic, it is a security and privacy standard designed to ensure the secure processing and storage of cardholder data. It has a single objective: to prevent sensitive cardholder data—such as card numbers and CVV codes—from leaking outside your system.
In this post, we’ll look at how to set up a simple architecture for processing card-not-present (i.e., e-commerce) payments. For example, you may have an e-commerce website and want to accept card payments via a form in your UI. You could take the easy route and embed your payment processor’s hosted payment form in an iframe, allowing you to complete a simple self-assessment instead of a full audit. However, you might have more complex requirements. Maybe you want to process payments on the backend to route transactions to different providers or apply custom retry logic to improve conversion rates.
If you process sufficiently large volumes, you will need to implement the full set of security requirements, run a successful ASV scan, perform penetration testing, and pass an audit conducted by a Qualified Security Assessor (QSA). This places you at PCI DSS Level 1, the highest level of certification.
PCI DSS Requirements
The PCI DSS standard defines six major requirement categories:
- Build and maintain secure networks and systems — configure network controls and ensure all components are securely hardened.
- Protect account data — securely store cardholder data (if required) and ensure encryption in transit.
- Maintain a vulnerability management program — protect all system components from malicious software and establish a secure software development lifecycle.
- Implement strong access control measures — establish identity and access management based on the principle of least privilege; enforce secure authentication and authorization; and limit physical access to infrastructure.
- Regularly monitor and test networks — monitor and audit access to system components and regularly test network security.
- Maintain an information security policy — document, maintain, and enforce organizational security policies.
Each category contains detailed requirements, and the exact controls depend on your use cases and infrastructure design. Later, we’ll look at a simple reference architecture on AWS using ECS Fargate.
Key Architecture Principles
Reduce the Scope of the Audit
PCI DSS requirements apply only to the parts of your system that process cardholder data, so minimizing this scope is critical. If you have a monolithic application where even a single API endpoint handles card data, the entire application—its infrastructure and supporting tools—falls under PCI DSS scrutiny. To avoid this, you should extract card data processing into a dedicated service running in an isolated environment. This ensures that only this narrowly scoped component is subject to audit.
Delegate Security Controls
Many PCI DSS requirements apply to physical infrastructure and operating system security. AWS removes responsibility for the physical layer, and managed services such as ALB, WAF, and ECS Fargate further offload OS-level and configuration-related security concerns. That said, you must still ensure that the AWS services you use are themselves PCI DSS compliant.
Avoid Storing Credit Card Data
Only store cardholder data if absolutely necessary. Otherwise, forward the data to your payment service provider (PSP) to execute the transaction and discard it immediately. Storing card data introduces an entirely separate set of PCI DSS requirements and significantly increases risk. By not storing this data, you can eliminate those requirements altogether.
Simple AWS Architecture Using ECS Fargate
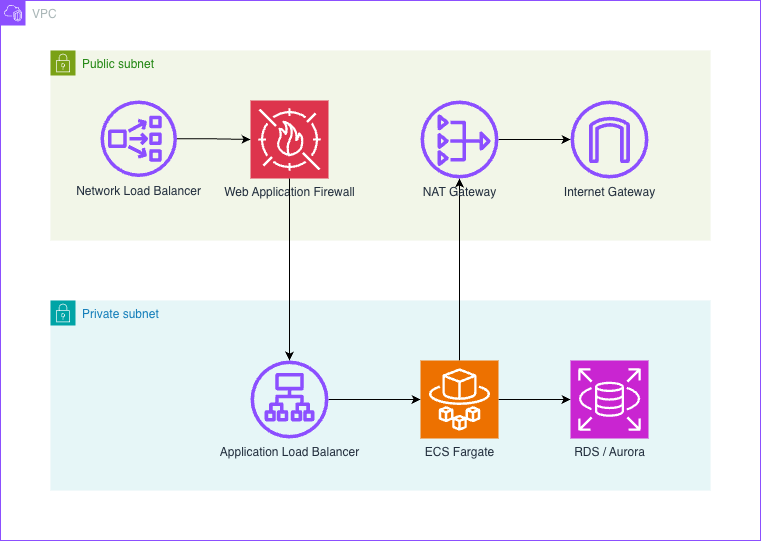
Let’s review how the previously mentioned requirements are addressed in this architecture:
- Build and maintain secure networks and systems — network security is enforced through AWS WAF and tightly configured security groups.
- Protect account data — cardholder data is not stored, and encryption in transit is handled by the Application Load Balancer.
- Maintain a vulnerability management program — using managed services like ECS Fargate removes the need to manage OS-level security, malware protection, and antivirus software. You still need a secure SDLC in your repositories and CI/CD pipelines, but that is outside the scope of this article.
- Implement strong access control measures — depending on your AWS setup, you can use IAM or IAM Identity Center for identity and access management. Note that if you use IAM Identity Center, your SSO provider also becomes part of the audit scope as a system impacting the cardholder data environment.
- Regularly monitor and test networks — infrastructure changes can be audited via CloudTrail, while security events can be monitored using AWS WAF and GuardDuty. With correct configuration, the ALB will also pass standard network security scans.
- Maintain an information security policy — security procedures must be documented regardless of cloud provider, but reducing scope significantly lowers operational and administrative overhead.
As shown, a substantial portion of the security burden is offloaded to AWS-managed services. Using ECS Fargate and related services allows you to avoid managing the operating system layer directly.
Summary
Achieving PCI DSS compliance can be particularly challenging for legacy monolithic applications. If any component processes cardholder data, the entire application—including its codebase, infrastructure, and personnel—falls within PCI DSS scope. A better approach is to isolate card data processing into a tightly controlled, standalone service.
If you’re building a greenfield system, this separation should be a core architectural decision from day one. While this article focuses on AWS, equivalent architectures are possible on Azure using Azure Container Services or on GCP using Cloud Run. Regardless of the platform, always be deliberate about managing and minimizing scope.
For a good starting point on PCI DSS, refer to the official document library, specifically the PCI DSS Quick Reference Guide.